There is already a thread on how to uninstall or deactivate most google apps (gapps)
from the FP3 stock Android9.
(Also relevant: ✏ How to live without Google on a Fairphone 3 (FP3) )
Unfortunately the google apps are not the only preinstalled components on the FP3 that have undocumented telemetry capabilities and regularly or sporadically talk home.
Some of these connections are rare (once a week, once a month, once after each reboot) so it becomes a community effort to itentify components that are potential snitches and share unknown amount of data about your phone and its usage with undisclosed third parties.
Regardless of whether or how one should get rid of those or not, I think its important to document this behavior, as it potentially impairs your privacy, data and device security.
If you have a firewall app or a Third party firewall on a router running and find that any preinstalled or auto-installed software component or app makes outgoing or accepts incoming connections without your explicit request, please add to this thread so we can document.
What app it is
What kind of communication it is
Whats the official purpose
and maybe
What is the data being communicated
and also maybe
What are potential alternatives if the app is required for the phone.
Don’t hesitate to include the obvious (google) apps here as well. I disabled most of them, so I start with the more exotic ones that popped up later.
System app “Phone” (com.google.android.dialer)
- Reason: Unexpected Background-Connection attempt to fra15s12-in-x0a.1e100.net port 443 (domain and associated IP belongs to google)
- More Info: Is there any alternative to the default Dialer app - that works on FP3?
- Identified via NetGuard app
- Required for normal operation: Yes
- Alternative: com.android.dialer from Lineage OS, see Is there any alternative to the default Dialer app - that works on FP3?
System app “Qualcomm Mobile Security” com.qualcomm.qti.qms.service.telemetry
- Reason: Unexpeced Background-Connection attempt (destination unknown)
- More Info: Google Apps keep reinstalling/ reactivating - #27 by athair_birb
- Identified via NetGuard app
- Required for normal operation: Likely not
- Alternative: Unknown
Unnamed System app “” (com.qualcomm.qti.qms.service.connectionsecurity)
- Reason: Unexpected Background-Connection attempt to tls.telemetry.swe.quicinc.com port 443 (Host/Domain belongs to Qualcomm)
- More Info: -
- Identified via NetGuard app
- Required for normal operation: Unknown
- Alternative: Unknown
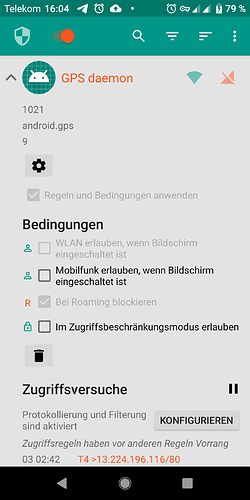
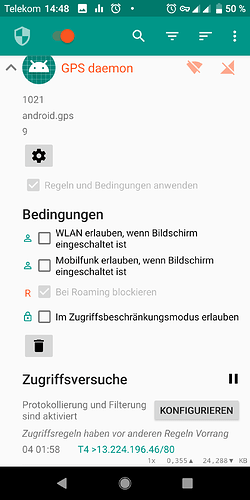
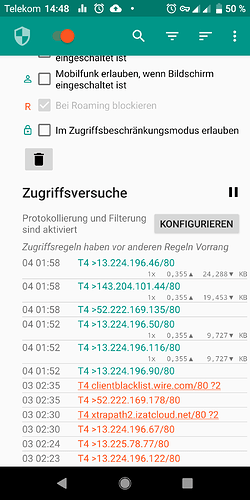
System app: “GPS daemon” (android.gps)
- Reason: Unexpected Background-Connection attempt to xtrapath1.izatcloud.net port 80 (belongs to Qualcomm) (and others)
- Frequency: During the night hours, often between 0:00 and 2:00 UTC
- More Info: Automatic retrieval of vendor specific GPS almanac, see Telemetry, Spyware, list of privacy threats on FP3 Android 9 - #5 by Johannes
- Identified via NetGuard app
- Required for normal operation: Needed for fast GPS fixes, optional
- Alternative: Unknown
- Notes:
- Can not be uninstalled without rooting
- HTTP request leak detailed information about device including serial numbers via User-Agent string. See post below Telemetry, Spyware, list of privacy threats on FP3 Android 9 - #25 by corvuscorax for tcp dump
System app: “Android System” ()
- Reason: Background-Connection attempt to port 123 via UDP
- Frequency: After each reboot
- More Info: UDP Port 123 is Network Time protocol. Android retrieves its system time from various time servers all over the world belonging to various organisations (most likely NTP pool servers
- Identified via NetGuard app
- Required for normal operation: Yes
- Alternative: None - time servers are not configurable in Android 9