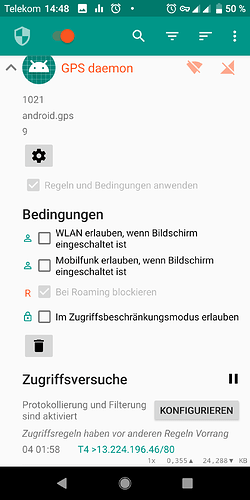
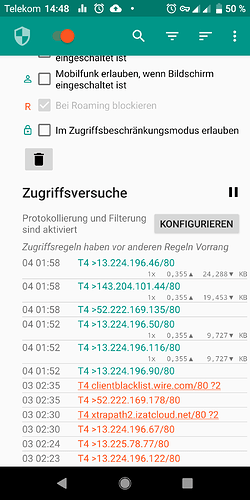
I finally managed to get a packet capture. The enigmatic GPS daemon finally decided to contact its masters again last night at 01:52 am. It looks like tries to indeed get binary (Almanach?) data roughly once every 24 hours, preferably past midnight.
capture.pcap (26.6 KB)
Over a time of 10 minutes, it retrieved the same file from multiple servers
GET /xtra3grc.bin HTTP/1.1
from
Host: xtrapath3.izatcloud.net ( binary size 32232 )
Host: xtrapath2.izatcloud.net ( binary size 23498 )
Host: xtrapath3.izatcloud.net ( binary size 32232 ) (same file again?)
Host: xtrapath1.izatcloud.net ( binary size 24347 )
The full request looks like this:
GET /xtra3grc.bin HTTP/1.1
Host: xtrapath3.izatcloud.net
Accept: */*, application/vnd.wap.mms-message, application/vnd.wap.sic
x-wap-profile: http://www.openmobilealliance.org/tech/profiles/UAPROF/ccppschema-20021212#
User-Agent: A/9/Fairphone/FP3/FP3/unknown/QCX3/l3557659004810866045/35781109/+111575957/-+262|01+262|03/Fairphone/36966/36953/-/3.0/1/W/0
with slight changes in user agent on the 2nd to 4th request:
User-Agent: A/9/Fairphone/FP3/FP3/unknown/QCX3/l3557659004810866045/35781109/+111575957/-+262|01+262|03/Fairphone/36969/36956/-/3.0/1/W/0
User-Agent: A/9/Fairphone/FP3/FP3/unknown/QCX3/l3557659004810866045/35781109/+111575957/-+262|01+262|03/Fairphone/37287/37274/-/3.0/1/W/0
User-Agent: A/9/Fairphone/FP3/FP3/unknown/QCX3/l3557659004810866045/35781109/+111575957/-+262|01+262|03/Fairphone/37287/37274/-/3.0/1/W/0
Interesting is the data revealed in the user agent. A/9 is obviously the OS, Android 9 Pie. Fairphone/FP3/FP3 seems to be manufacturer, model number and board. 35781109 I identified as the first 8 digits of the IMEI - also known as TAC (type allocation code) (this is identical for both SIM card slots)
I could not identify the long number, it is likely some sort of serial number.
It’s safe to assume that Qualcomm deliberately packed a lot of detailed identification data into this user agent string - probably more than enough to identify and track individual users, especially since some of the information is run time information changing between every request.
It’s possible that the 2 changing fields indicate what state information the phone is in. This is speculation, but since the phone did not learn new information by re-downloading the binary from xtrapath3.izatcloud.net, it sent the next GET request with the same identifiers.
I managed to get that pcap on the phone itself by letting WireGuard run over night with packet capturing enabled:
It’s interesting to note that GPS daemon cannot be disabled or uninstalled without rooting the device, since it does not even show in the list of installed applications (pm list packages) or running system services. The only way to prevent this data exchange is to leave wifi and data turned off during the night (or whenever GPS daemon tries to retrieve it) OR to install a firewall on the device that prevents this based on App/UserID.