I hope somebody can help me with this:
How do you check (if at all) the integrity of the apk you download from f-droid.org ? Because basically after that I will/have to trust that app(store).
Usually I’d check the MD5 sum, but searching for the result there does not seem to be an officially published one, just a bunch of mirror sites.
Obviously my question was already asked on the f-droid forums and someone pointed to the GPG key. Now I am at loss. How do I (using e.g. a Mac) check the apk file for integrity using its GPG key?
APK are signed obligatory for authorship and integrity. Android automatically checks if the APK has been tampered and refuses to install it if so (integrity). When applying updates, Android checks if the signatures between updates match, and refuses to install it if they mismatch (authorship).
So you’re left only to check the authorship for the first APK you install (for each app). It should be a CLI tool for that in the Android SDK (inside platform-tools, maybe). I’ll check later today, 
Apparently there is a tool for this included in the Android SDK Build Tools revision 24.0.3 and above: apksigner. Unfortunately I only have 23.0.2 installed, so I can’t verify right now. 
I’m sorry, I am pretty new to all this (android and GPG) and do not really understand your replies.
So I installed Fairphone open, that worked just fine. Then I downloaded F-Droid. Now to install F-Droid I have to allow unknown sources. Thus I’d like to check the f-droid.apk before installing it. But how? The f-droid forums pont to GPG. I tried this (here only for Tor) https://www.torproject.org/docs/verifying-signatures.html.en with the public key of admin@f-droid.org, but it always fails. It works just fine with the tor dmg. But as I said, considering the GPG stuff (just following instructions from the Tor page) I do no really know/understand what I am doing
I haven’t tried this either, so I can’t help any further. Anyway, I moved this discussion to #software so hopefully it will be more visible so that other can provide you with a solution.
For reference: Here is the F-Droid Wiki entry about the signing keys.
Thanks everyone! I just realized, however, (also because the topic was split) that my original question could easily be missunderstood.
What I want to check is the f-droid app itself (fdroid.apk) not so much (actually not at all) apps I download from f-droid. So to speak setting some foundation for my trust in f-droid.
Given I trust the f-droid “client” I’d just trust the apps I can download from there.
I have no idea about keys and all that, but if you trust the apps on f-droid - which I totally understand - then why wouldn’t you trust the client app you download from their official website?
A pinch of paranoia, or rather just wanting to make it “right”.
A compromised (incredibly unlikely) f-droid client undermines all trust in any app one will download in the future. An attacker “just” had to fake the f-droid webpage, with a manipulated client. From then on doors are open.
It must be a method for checking it for security hygiene (check Signal, for example)
True
F-Droid page is served under HTTPS (TLS), so hijacking the connection (MitM attack) is practically impossible. But, it should be a method to check the APK, anyway.
I know, I also checked the connection prior to downloading. I was, however, surprised that checksums are not more widely communicated (i.e. actually checked by people) and that F-Droid argues that a checksum communicated on the webpage itself is pointless (if the apk file is faked because of an elaborate man in the middle attack then of course the checksums will be too) but at the same time offer no how-to for checking the integrity.
Also, the next person with a similar question will probably rage at this point, as I complain about the absent of checksums but do not publish the one I obtained
So here is what I get for the FDroid.apk (the one that downloads via the huge download button)
MD5 : 0f31429a28619e824669c3e5144fcdd4
The huge download button doesn’t give you the GPG signature of the apks, so you need to go to https://f-droid.org/repository/browse/?fdfilter=f-droid&fdid=org.fdroid.fdroid, as linked to in the wiki entry.
- Download the apk and the GPG signature for the latest version.
- Download the public key (I found it at pgp.mit.edu). Type:
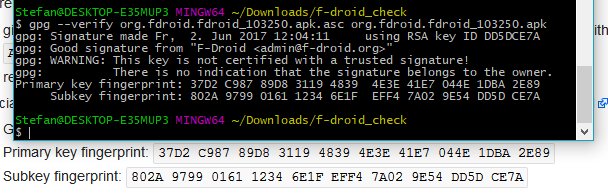
gpg --keyserver pgp.mit.edu --recv-keys 0x41e7044e1dba2e89 - Verify the signature. Type:
gpg --verify org.fdroid.fdroid_103250.apk.asc org.fdroid.fdroid_103250.apk - If you did everything correctly, the following output should appear. Check if the fingerprints match!
Hello,
I hope my answer will be helpful (and I hope I won’t repeat something already said here). Apparently you have to install Android-Studio if you want to verify F-Droid’s app key (which I didn’t, blame myself), because ADB doesn’t seem to provide any command for this : there is none listed here : https://developer.android.com/studio/command-line/adb.html. As @Stefan said, you can then use the apksigner command.
Apparently, there is a difference between a GPG signing key and and APK signing key, if you look at F-Droid’s wiki here : https://f-droid.org/wiki/page/Release_Channels_and_Signing_Keys. As I didn’t do researches about this, I only can suppose that the main difference between them is their original author : GPG is the libre version from PGP and is given to us by GNU and the FSF (Free Stoftware Foundation) if I am not mistaken. APK signing key, I suppose, comes from Google.
If you look at the F-Droid wiki page I linked here, it seems that you can use both technologies to verify the F-Droid app. On GNU/Linux machines (as on mine for example), GPG is present by default, but for Mac and Windows you need to download it, with a graphical tool for Windows and you also have this option for Mac : https://gpgtools.org/gpgsuite.html. But I just remembered Mac users can also use the command line ! I don’t know if you can install a command line tool for GPG on Mac, but it you want to try you need to install homebrew, which is the equivalent of apt-get (Debian, Ubuntu) or pacman (Arch Linux) for Mac. The official website of the project tells you how : https://brew.sh/. Maybe there is a DMG file in the App store too.
If (too much ‘if’, sorry) there is a GPG command line tool for Mac, here is the command manual for GPG : https://www.tutorialspoint.com/unix_commands/gpg.htm.
Thanks! I saw that too, but have not tried it yet. Most of all, because I am rather confused by what they write right next to the download button. Quote:
“Although APK downloads are available below to give you the choice, you should be aware that by installing that way you will not receive update notifications, and it’s a less secure way to download. We recommend that you install the F-Droid client and use that.”
To me this reads like one should rather go with the download button (I already did that and in this case the F-Droid client offers an update once installed), but I do not know why the other options are “less secure” and you then do “not receive update notifications”. Isn’t the file you get via the download button just an older version, should it not be just some of the files in the list of all later builds?
Ok, now I finally get some result. However, I still do not really know how to interpret it. Basically the tutorials in the f-droid forums are probably what I also did. However it never worked, and I still do not know what I did wrong (maybe I renamed the file and changed the name back to the original?)
So here is just a short synopsis.
On OSX you need GPGtools or something similar. Then import the pubic key of F-Droid (admin@fdroid.org), can be found on keyservers, just search for it in GPG’s keychain.
Download the FDroid.apk via the download button.
Download the .asc file from here (what is this? Some sort of script, what does it do?)
https://f-droid.org/forums/topic/client-apk-sha-checksum/
Then move both files to the same folder and make sure the asc file has the name of the FDroid client (in case you renamed it, originally it should be “FDroid”) followed by .apk.asc. On OSX you can now either work with the terminal just as in the tutorial considering Tor, or there also is a dropdown menu (right click on the apk file) OpenPGP: "Verify Signature of File"
Following these steps I now also get “a signed by…”
The big download button just makes it easier for people to install F-Droid for the first time. That message is a generic one, shown in the repo page for each app. It means:
- if you aren’t downloading from F-Droid itself, you won’t receive updates (because you may not have F-Droid installed)
- and you are avoiding the verification F-Droid app do for itself.
Obviously the first point doesn’t have sense if you are downloading F-Droid. The second point is the verification that we are discussing right here.
I agree with the argument that some verification method should be shown or linked under the big button. (See the P.S. edit below)
Also, the big button lets you download the most recent stable version of F-Droid (right now, 0.102). From the repo page for F-Droid app you can download any version, including release candidates (like 0.103-alpha1 onwards to 0.103.2)
Edit: A GPG key seems to exist on https://f-droid.org/FDroid.apk.asc for the big button APK (https://f-droid.org/FDroid.apk). It matches with the 0.102 release GPG (https://f-droid.org/repo/org.fdroid.fdroid_102050.apk.asc)
P.S.: We should notify these issues to the F-Droid team!
Edit: Let’s see if we can solve this from the begining in the next website: https://gitlab.com/fdroid/fdroid-website/merge_requests/83
All GnuPG versions can be downloaded from GnuPG’s website. For Windows there is not only the command line tool, but also a graphical tool called Gpg4win (which includes GnuPG).
This topic was automatically closed 182 days after the last reply. New replies are no longer allowed.