it would be interesting to find out which apps/components phone home even despite the user having skipped/declined the agreements. There shouldn’t be any, as that’d be most likely illegal, but I have a hunch at least the Qualcomm stuff and most likely also many gapps will contact their servers when given the chance.
I’ve reset my device, accepted the Google EULA and that’s it. I did not configure an account or added any other apps. Just factory default settings.
I also did not use the FP3 for a week. it was just lying there on my desk without SIM card
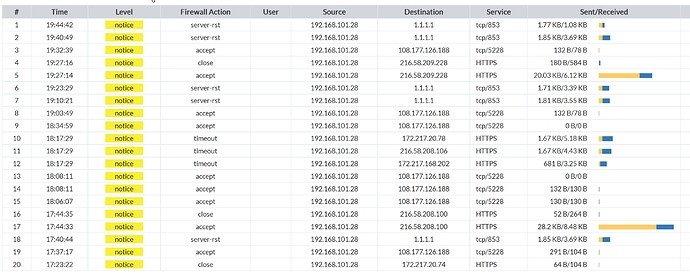
I now have a week of FortiGate logs to analyse…
There are a lot of calls going out (2259 calls and about 280MB on data), most of them towards google domains but also some undefined IP addresses which I still need to verify
I’ll see if I can setup a new test when refusing Google EULA
It is not possible to refuse Google privacy agreement. You cannot pull down the notification bar. I also tried in safe mode, but it didn’t work.
Lol the moderator has deleted my reply. 280MB in one week is not acceptasble. The Flatrate from aldi talk is only eaten by the phone itself!!!:
https://www.alditalk.de/jahrespaket
what is talking home? what data is collected for 280mb/week???
It seems external firewalls are pretty useless to analyze what an Android phone is talking “home” for several reasons:
- An external firewall can only see the port a connection is originating from, not which app/program is making the connection
- An external firewall can only see the IP address a connection is made to, not the domain (unless using deep packet inspection)
- Most “telemetry services” are using the very same content delivery networks the majority of webpages are using such as Amazon AWS, Cloudflare, Microsoft Azure and Google Cloud, to name the probably largest ones. That leads to several effects which make it almost impossible to block these accesses:
- each service uses very large, distributed pool of IP addresses, which can change or be extended daily and there’s no reliable complete lists
- each of these IP addresses are also used by a large number of legitimate internet connections, such as chat apps, games, etc… and blocking them would cause massive colateral damage
- the majority of these connections is encrypted using TLS/HTTPS.
Using deep packet inspection, it is be possible to identify the domain names used in each access and prevent the connections, as these are transferred unencrypted in some TLS requests to allow the server to chose the appropriate certificate, but that reqires advanced firewalls, especially if these connections are to be reliably blocked without also blocking legitimate connections to the same hosts on a per-connection base
The easier option, although potentially less secure is IMHO a local firewall solution on the device. This can identify or at least narrow down which app or service is responsible for an outgoing network connection.
Without rooting the device, the best options are VVPN (virtual VPN) apps, which pretend to provide internet access through a VPN - which is routed only through a local loopback connection (VPN server and client both run on the android device)
One such option is NetGuard, which is available in both Google Appstore, Fdroid and directly from Github. https://github.com/M66B/NetGuard
Another option are genuine VPN services, preferably with a VPN server under one’s own control.
A rooted phone would of course offer more possibilities.
Just to be sure, it might make sense to use an external firewall on top of the local one, to find out if there are any apps/services capable in bypassing a local firewall and routing rules. Since some of the suspect system services have root privileges, this is theoretically possible and probably should be checked.
@Linus I would suggest to install a local firewall such as Netguard to identify which app is responsible for creating that much traffic, and to block such if necessary.
On my phone I never had that much, but I also did some configuration changes such as disabling automatic app updates in the google appstore and disable media downloads when on cellphone-data in some apps such as messengers.
In the default installation the appstore will auto-download and install any app updates, which depending on the apps installed and affected can easily be in the hundreds of megabytes. I am not sure if it will do that over cellphone-data by default or not, but it might be worth checking.
By default, the Play Store downloads app updates via Wi-Fi only. So no worries here. I have no idea whether alternative app stores act differently in that respect, because I do not use any.
Seeing 1.1.1.1:853 in the list is Cloudflare, not Google (theirs is 8.8.8.8 and 8.8.4.4), and it is their DNS over TLS given it uses port 853. You give Cloudflare (instead of anyone who snoops your line) access to your DNS requests. This is read access, to a large company, but the alternative is arguably worse. Especially in the USA where ISPs inject crap via DNS (no joke!). I’m unsure if Cloudflare(/Google/IBM) have write access to the requests (ie. can spoof replies).
I am not so sure. I think what’s running might not be “Qualcomm Location” but instead " XTRA – Predicted GNSS Satellite Orbit Data" as written about here: Privacy Policy | Qualcomm
The relevant section might then instead be:
XTRA uploads the following data types: a randomly generated unique ID, the chipset name and serial number, XTRA software version, the mobile country code and network code (allowing identification of country and wireless operator), the type of operating system and version, device make and model, the time since the last boot of the application processor and modem, and a list of our software on the device
This looks approximately consistent with what you were seeing in the user-agent string, right?
It’s still some information disclosure to upload that information (and not even over HTTPS, so any MITM can read as well!), but not at all as bad as GPS locations and Wifi towers.
To add to the previous post; this does not exclude that there actually is some other service that is “Qualcomm Location”, but a quick googling seems to show that there seems to be “com.qualcomm.location” services on some other phones. So based on that, my guess is that “Qualcomm Location” is not installed on the FP3.
there are a number of qualcomm services running on the fairphone, including “connection security” and “telemetry” - they communicate encrypted, so we do not know what they transfer.
The only service that connects unencrypted is the GPS daemon. (Which technically is not a “service” in the classical sense. There is no app for it, it’s running on driver level and cannot be stopped/killed/disabled through adb)
It transfers a string as part of the user agent that is both device specific and state specific (parts of the string change with every request) - the data volume sent is not enough to include a complete location history though, but it is potentially enough to encode the current location at the time of the request.
that being said, the main purpose of this unencrypted request is to update the GPS Almanach, which is usually done before a GPS lock can be established.
Looking at the user agent strings you provided, the parts that change are two numbers that increase slightly and the difference between them is always “13”. It seems likely to me that this is the “time since the last boot of the application processor and modem”, i e the uptime.
Have you checked whether they use certificate pinning? Have you tried mitmproxy/sslstrip?
no – that is on my TODO list for a while, but I currently don’t have the time for exhaustive forensics.
Another option, if it does use pinning, you could disassemble and reassemble the apps involved with smali/baksmali and change a few strings (such as the server URLs) - unless the communication in question is done by native compiled crap, this might be the quickest way to find out what is transferred.
Of course you could find out its encrypted crap coming straight from the QSEE enclave. (Qualcom’s DRM stuff, running on a privileged hyperkernel above the linux kernel) in which case you would be as wise as before.
After upgrading to Android 10, there’s various new apps and services on the phone that send data to third parties. Some of them can not be deactivated.
For example, after upgrade I caught my phone in flagranti trying to make a connection to “activation.fairphone.com” port 10780. The connection is initiated by a service running with user ID 1000 - sadly I could not identify which one - this includes quite a number of services including a new system app called “Fairphone Activator” (com.fairphone.activator) – This app has access to the phone and the phone location, which can not be disabled in the settings. The app also can not be disabled or uninstalled.
WHAT THE F*****? FAIRPHONE???
It’s bad enough that we have all this Qualcomm Spyware preinstalled which calls home all the time, but I cannot remember agreeing that fairphone is collecting data about my phone or its whereabouts.
I am going to call support, ask what kind of data this service transfers, and I am going to ask for a way to inhibit this.
I sent the following support request. Let’s see what the answer is:
After updating the Phone to Android10 with the recent over-the-air upgrade.
A new system app called “Fairphone Activator” has been installed.
(com.farphone.activator)
This app has access to the Phones internals as well as it’s location and
sends data to activation.fairphone.com TCP port 10780 as well as fp.thingslot.com and other URLS…I do not want that. I am a quite sensitized to privacy threads on consumer devices. This is one of the main reasons why I bought a Fairphone in the first place, since I was under the impression that Fairphone - unlike many other phone manufacturers - would NOT spy on their users.
I was quite shocked that the phone would now do that without prior notification or consent.
I tried to disable the app, but this is not possible, since it is a system app.
It also was not possible to uninstall it.Then I tried to disable the apps access to the phone’s location and system internals
(in the app permissions) but the option to change the permission is greyed out with the notice “Device requires this permission to operate”.This is obviously not the case, since the Device operated fine without this app prior to the Android10 upgrade, and the device worked fine while the network access was being blocked.
In accordance with the EU GDPR directive I have the right to know what kind of data Fairphone collects about my phone usage and for which purpose. Data like IMEI and Phone location, which this app has access to is personal information capable of identifying and tracking individuals.
The phone should not transfer any data to Fairphone or any 3rd party without prior notification and permission of its user - unless the user explicitly requested this by performing an operation that implies this data transfer (such as performing a search, phone call, or accessing a webpage) No such permission or intent was given.
I expect you to provide detailed information to me, which I will share with the community in the appropriate forum threads:
- What does this app do, what is its purpose
- What data is being collected/send to fairphone.com
- How can this app can be disabled/uninstalled
- Why was this app shipped in the first place without informing users or asking for consent to its operation.
best regards,
Interesting find. I took a look into the code. Looks like this app will check on every reboot if the current build has been “actived” yet (meaning data being uploaded). If not the case, it will upload the following information to the URL you mentioned:
Generic build and device infos:
BRAND
BUILD_ID
BUILD_TIME
FINGERPRINT
MODEL
OS_VERSION
Serial
It will also contain the following personal information and location data (LTE cell info for each SIM):
IMEI1
IMEI2
LANGUAGE
LTE_GCID_1
LTE_GCID_2
LTE_LAC_1
LTE_LAC_2
LTE_MCC_1
LTE_MCC_2
LTE_MNC_1
LTE_MNC_2
LTE_OPERATOR_NAME_1
LTE_OPERATOR_NAME_2
Since the app cannot be deactivated. uninstalled, or its access rights revoked, I tried to get rid of it using adb shell:
pm uninstall --user 0 com.fairphone.activator
I am not 100% sure if this also works after a cold reboot, or if there’s a brief window of opportunity for the app to become active if there is internet (WIFI or mobile data) while the phone is still being unlocked, as the user data - including the information about app permissions and preferences - might still not be loaded yet. I simply don’t know well enough how the android boot process works in relation to user-uninstalled-apps.
Hi, have you already received answers about the spy features?