Good morning ![]()
In the end you are right and …
O M F G
what can I say?
I did it after reading the repartition-Link.
And it worked a 100% like a charm (or how do I say it correctly?).
Why are you @hirnsushi not an Fairphone-Angel?
In the end you also helped @bookworm, too in repartitioning.
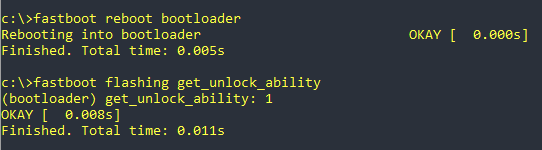
Anyway, the outputs (just for the protocol), Success:
But first I set the path variable to my adb-platform-folder, so that I didn’t have to replace the path to IMG-Files and I was able to copy/paste the commands from the Howto.
I started by booting into the bootloader and rebooted into it again, just to make sure, that the commands are working with the new path entry.
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot reboot bootloader
Rebooting into bootloader OKAY [ 0.001s]
Finished. Total time: 0.006s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash bluetooth_a bluetooth.img
Sending 'bluetooth_a' (940 KB) OKAY [ 0.030s]
Writing 'bluetooth_a' OKAY [ 0.005s]
Finished. Total time: 0.077s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash bluetooth_b bluetooth.img
Sending 'bluetooth_b' (940 KB) OKAY [ 0.029s]
Writing 'bluetooth_b' OKAY [ 0.005s]
Finished. Total time: 0.075s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash devcfg_a devcfg.img
Sending 'devcfg_a' (42 KB) OKAY [ 0.012s]
Writing 'devcfg_a' OKAY [ 0.002s]
Finished. Total time: 0.043s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash devcfg_b devcfg.img
Sending 'devcfg_b' (42 KB) OKAY [ 0.004s]
Writing 'devcfg_b' OKAY [ 0.002s]
Finished. Total time: 0.026s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash dsp_a dsp.img
Sending 'dsp_a' (65536 KB) OKAY [ 1.613s]
Writing 'dsp_a' OKAY [ 0.139s]
Finished. Total time: 1.803s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash dsp_b dsp.img
Sending 'dsp_b' (65536 KB) OKAY [ 1.559s]
Writing 'dsp_b' OKAY [ 0.171s]
Finished. Total time: 1.775s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash modem_a modem.img
Sending 'modem_a' (146188 KB) OKAY [ 3.665s]
Writing 'modem_a' OKAY [ 0.331s]
Finished. Total time: 4.057s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash modem_b modem.img
Sending 'modem_b' (146188 KB) OKAY [ 3.566s]
Writing 'modem_b' OKAY [ 0.360s]
Finished. Total time: 3.971s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash xbl_a xbl.img
Sending 'xbl_a' (3298 KB) OKAY [ 0.090s]
Writing 'xbl_a' OKAY [ 0.013s]
Finished. Total time: 0.165s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash xbl_b xbl.img
Sending 'xbl_b' (3298 KB) OKAY [ 0.084s]
Writing 'xbl_b' OKAY [ 0.011s]
Finished. Total time: 0.134s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash tz_a tz.img
Sending 'tz_a' (2944 KB) OKAY [ 0.076s]
Writing 'tz_a' OKAY [ 0.011s]
Finished. Total time: 0.126s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash tz_b tz.img
Sending 'tz_b' (2944 KB) OKAY [ 0.077s]
Writing 'tz_b' OKAY [ 0.011s]
Finished. Total time: 0.130s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash hyp_a hyp.img
Sending 'hyp_a' (399 KB) OKAY [ 0.021s]
Writing 'hyp_a' OKAY [ 0.004s]
Finished. Total time: 0.067s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash hyp_b hyp.img
Sending 'hyp_b' (399 KB) OKAY [ 0.019s]
Writing 'hyp_b' OKAY [ 0.004s]
Finished. Total time: 0.048s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash keymaster_a keymaster.img
Sending 'keymaster_a' (257 KB) OKAY [ 0.015s]
Writing 'keymaster_a' OKAY [ 0.004s]
Finished. Total time: 0.053s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash keymaster_b keymaster.img
Sending 'keymaster_b' (257 KB) OKAY [ 0.011s]
Writing 'keymaster_b' OKAY [ 0.004s]
Finished. Total time: 0.049s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash abl_a abl.img
Sending 'abl_a' (148 KB) OKAY [ 0.011s]
Writing 'abl_a' OKAY [ 0.004s]
Finished. Total time: 0.045s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash abl_b abl.img
Sending 'abl_b' (148 KB) OKAY [ 0.012s]
Writing 'abl_b' OKAY [ 0.004s]
Finished. Total time: 0.033s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash boot_a boot.img
Sending 'boot_a' (98304 KB) OKAY [ 2.424s]
Writing 'boot_a' OKAY [ 0.221s]
Finished. Total time: 2.697s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash boot_b boot.img
Sending 'boot_b' (98304 KB) OKAY [ 2.373s]
Writing 'boot_b' OKAY [ 0.231s]
Finished. Total time: 2.666s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash recovery_a recovery.img
Sending 'recovery_a' (98304 KB) OKAY [ 2.474s]
Writing 'recovery_a' OKAY [ 0.231s]
Finished. Total time: 2.762s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash recovery_b recovery.img
Sending 'recovery_b' (98304 KB) OKAY [ 2.409s]
Writing 'recovery_b' OKAY [ 0.243s]
Finished. Total time: 2.689s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash dtbo_a dtbo.img
Sending 'dtbo_a' (24576 KB) OKAY [ 0.616s]
Writing 'dtbo_a' OKAY [ 0.056s]
Finished. Total time: 0.730s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash dtbo_b dtbo.img
Sending 'dtbo_b' (24576 KB) OKAY [ 0.596s]
Writing 'dtbo_b' OKAY [ 0.057s]
Finished. Total time: 0.691s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash vbmeta_system_a vbmeta_system.img
Sending 'vbmeta_system_a' (4 KB) OKAY [ 0.012s]
Writing 'vbmeta_system_a' OKAY [ 0.002s]
Finished. Total time: 0.063s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash vbmeta_system_b vbmeta_system.img
Sending 'vbmeta_system_b' (4 KB) OKAY [ 0.006s]
Writing 'vbmeta_system_b' OKAY [ 0.002s]
Finished. Total time: 0.051s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash vbmeta_a vbmeta.img
Sending 'vbmeta_a' (8 KB) OKAY [ 0.002s]
Writing 'vbmeta_a' OKAY [ 0.001s]
Finished. Total time: 0.021s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash vbmeta_b vbmeta.img
Sending 'vbmeta_b' (8 KB) OKAY [ 0.009s]
Writing 'vbmeta_b' OKAY [ 0.002s]
Finished. Total time: 0.044s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash super super.img
Sending sparse 'super' 1/4 (780797 KB) OKAY [ 20.677s]
Writing 'super' OKAY [ 0.002s]
Sending sparse 'super' 2/4 (751633 KB) OKAY [ 27.026s]
Writing 'super' OKAY [ 0.002s]
Sending sparse 'super' 3/4 (726194 KB) OKAY [ 19.988s]
Writing 'super' OKAY [ 0.002s]
Sending sparse 'super' 4/4 (586888 KB) OKAY [ 22.007s]
Writing 'super' OKAY [ 0.002s]
Finished. Total time: 91.259s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash aop_a aop.img
Sending 'aop_a' (174 KB) OKAY [ 0.016s]
Writing 'aop_a' OKAY [ 0.004s]
Finished. Total time: 11.880s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash aop_b aop.img
Sending 'aop_b' (174 KB) OKAY [ 0.011s]
Writing 'aop_b' OKAY [ 0.004s]
Finished. Total time: 0.037s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash featenabler_a featenabler.img
Sending 'featenabler_a' (84 KB) OKAY [ 0.005s]
Writing 'featenabler_a' OKAY [ 0.003s]
Finished. Total time: 0.034s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash featenabler_b featenabler.img
Sending 'featenabler_b' (84 KB) OKAY [ 0.006s]
Writing 'featenabler_b' OKAY [ 0.004s]
Finished. Total time: 0.028s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash imagefv_a imagefv.img
Sending 'imagefv_a' (524 KB) OKAY [ 0.022s]
Writing 'imagefv_a' OKAY [ 0.004s]
Finished. Total time: 0.057s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash imagefv_b imagefv.img
Sending 'imagefv_b' (524 KB) OKAY [ 0.021s]
Writing 'imagefv_b' OKAY [ 0.004s]
Finished. Total time: 0.064s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash multiimgoem_a multiimgoem.img
Sending 'multiimgoem_a' (13 KB) OKAY [ 0.009s]
Writing 'multiimgoem_a' OKAY [ 0.002s]
Finished. Total time: 0.044s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash multiimgoem_b multiimgoem.img
Sending 'multiimgoem_b' (13 KB) OKAY [ 0.011s]
Writing 'multiimgoem_b' OKAY [ 0.001s]
Finished. Total time: 0.039s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash qupfw_a qupfw.img
Sending 'qupfw_a' (53 KB) OKAY [ 0.010s]
Writing 'qupfw_a' OKAY [ 0.003s]
Finished. Total time: 0.041s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash qupfw_b qupfw.img
Sending 'qupfw_b' (53 KB) OKAY [ 0.008s]
Writing 'qupfw_b' OKAY [ 0.002s]
Finished. Total time: 0.028s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash uefisecapp_a uefisecapp.img
Sending 'uefisecapp_a' (121 KB) OKAY [ 0.012s]
Writing 'uefisecapp_a' OKAY [ 0.003s]
Finished. Total time: 0.068s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash uefisecapp_b uefisecapp.img
Sending 'uefisecapp_b' (121 KB) OKAY [ 0.012s]
Writing 'uefisecapp_b' OKAY [ 0.003s]
Finished. Total time: 0.035s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash xbl_config_a xbl_config.img
Sending 'xbl_config_a' (94 KB) OKAY [ 0.007s]
Writing 'xbl_config_a' OKAY [ 0.006s]
Finished. Total time: 0.039s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash xbl_config_b xbl_config.img
Sending 'xbl_config_b' (94 KB) OKAY [ 0.009s]
Writing 'xbl_config_b' OKAY [ 0.004s]
Finished. Total time: 0.032s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash core_nhlos_a core_nhlos.img
Sending 'core_nhlos_a' (108556 KB) OKAY [ 2.751s]
Writing 'core_nhlos_a' OKAY [ 0.263s]
Finished. Total time: 3.066s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot flash core_nhlos_b core_nhlos.img
Sending 'core_nhlos_b' (108556 KB) OKAY [ 2.623s]
Writing 'core_nhlos_b' OKAY [ 0.250s]
Finished. Total time: 2.923s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot erase userdata
******** Did you mean to fastboot format this ext4 partition?
Erasing 'userdata' OKAY [ 0.733s]
Finished. Total time: 0.762s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot erase metadata
Erasing 'metadata' OKAY [ 0.018s]
Finished. Total time: 0.034s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot --set-active=a
Setting current slot to 'a' OKAY [ 0.027s]
Finished. Total time: 0.041s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot.exe getvar current-slot
current-slot: a
Finished. Total time: 0.006s
c:\IMG-e-1.4-r-20220920220047-stable-FP4>fastboot reboot
Rebooting OKAY [ 0.000s]
Finished. Total time: 0.008sIt was easier than the easy-installer from /e/os website, I’m gonna delete it ![]()
The whole install-procedure via CMD took less time than uninstalling easy-installer. ![]()
Thank you, Thank you, Thank you.
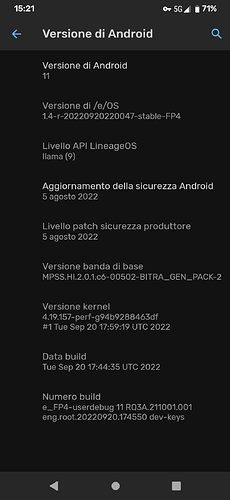
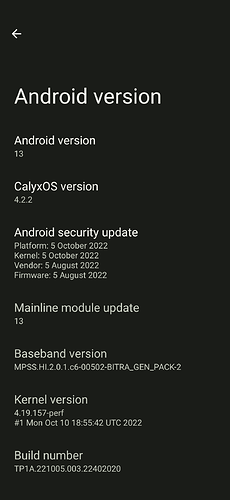
It started up without any errors.
Best regards
Salsa