What you could do is power the phone while open. It won’t be able to actually boot, but the bootloader should give out some UART debug output even with most periphery disconnected. Enough to identify the correct pad with a probe (without actually soldering anything to the pads - yet)
Of course that only makes sense if you actually have an oscilloscope (or at least a software-oscilloscope on a USB stick) and a probe 
The physical placement of the pads can be a hint (although no guarantee) about what is what. Pad’s A-F are next to the Wifi chip and the connectors to the side- buttons, (power, vol up+down) so it’s likely they debug that functionality
Pad’s G-Q are between CPU and the connector to fingerprint, backcamera, speaker, etc… - as such they could be anything, but some have already been identified to be connected to fingerprint sensor stuff
Pad’s R,S,T are between CPU and SD-card … there isn’t really anything debug-worthy on an SD-card, so the most likely thing would be something CPU related, like a debugging serial port (but could be something as stupid as power management, which is on the other side of the motherboard in the same area)
Pad’s U,V,W are nestled between sim cards, which are next to the RF modem, so they might be GSM debugging related stuff, or related to the display or NFC chips (which are on the other side of the board in the same location)
That’s why I think R-S-T are the most likely candidate, they tick all the boxes:
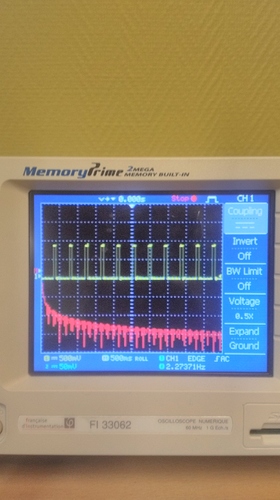
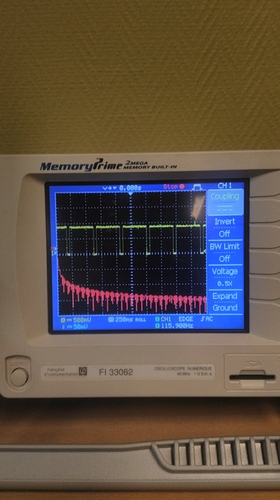
1: There’s three of them (which you need for UART)
2: One of which seems to be pulled up (which you’d expect from UART Rx)
3: One of which seems to be GND (which you need for UART)
4. They are next to the CPU
5. They are not next to an obvious alternate candidate
6. They are in a place from which you can relatively easily route a cable to the outside (at least with removed back-cover) using the opening for the sdcard
But I haven’t measured anything myself yet, so above is only an indication, no proof.
 .
.