The A11 beta has it enabled and working atm, so it does have WPA3 which was disabled on A10 after user problems as well AFAIK. Don’t know if both will get lost for the final release or afterwards.
WPA3 support renabled would be great news, would really like to use it on my FP3.
Hi joe.is.asking.2
MAC addresses can be spoofed on much devices/machines on a software level.
This indeed can support the idea obfuscating the tracking of a person - at first glance.
I played around with this topic some years ago on a few of my computers but I dropped it because you got to dive really deep into networking topics to make it work properly.
The second (and more important) argument why I dropped it: It´s just one tiny little piece of information to spoof an identity.
It´s well known that MAC adresses (all alone) are not reliable to track a user because it can be changed easily (at least on other devices).
The browser and apps you are using, their settings, addons, versions, the OS that app/browser runs on … all that talks much more about who is acting on a device, when and from where.
If someone wants to track you this tracking will not take just one piece of information into account like the MAC address but also dozens of more data items. Most of them are “under the radar” of a normal user.
Just as an example:
Imagine you order a gift from any shop and within that imagine your forename would be equivalent to a MAC address:
Will you receive that package if you change your postal address from:
John Doe, Livingstone street 12, London, UK
to:
Jackie Doe, Livingstone street 12, London, UK ?
I think you will receive the package and they will find you by the other information of your full address even if you spoofed your MAC address (=forename) ![]()
You can also do a practical example to see how trackable you are just with your browser:
It really opened my eyes and made me forget about the efforts & challenges of MAC spoofing ![]()
If you want to dive deeper into that rabbithole here a small starting point:
All in all I also would like to see this feature implemented soon.
But I see it less critical.
On a mobile there are much more wide open and also much bigger doors to identify a user ![]()
Best
DonFnord
Isn’t a point of “being unique” to be trans-platform traceable by behavior? If Iam on the same device and the amiunique webpage is incapable to join both attempts, then it is like it had done a perfect CT imagery of my body but once Iam taking a breath there is a new unique data point already… is there somewhere a more appropriate approach to mimic user identification done by google?
Nope … not at all trans-platform traceable.
That´s not the intention of that page.
Read the second headline (the one just under the headline … and maybe the first sentence of the purpose ![]() ) then you got it.
) then you got it.
Best
DonFnord
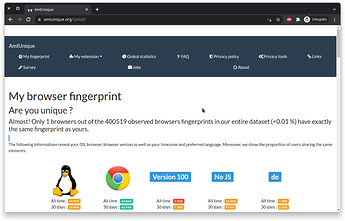
Of course I did. And in my understanding a fingerprint is to identify my machine, not my single webpage loading. Try it yourself please. If you visit that same page two times in a row, on same browser, without installing anything in between, without visiting any other website - how can my browser still show another “unique” fingerprint?
What this site does, is rise attention in the leakages of a browser. However it does not enable insight into identification by claiming this site visit left a unique fingerprint. Iam saying, it is an artificial setup. It doesn’t enable session identification, nor trans-device identification. The whole advertisement might lead to misinterpretation: namely that there is no problem at all - cause if every webpage load is unique, then tracing a user is impossible. Of course that is not what it is said here, but their setup simply can’t identify my machine by this fingerprint - so it is not a well chosen fingerprint.
If I wanted to implement a “unique fingerprint” I’d embed a calculation that prints out a different result every time it is run. The audio test etc feel like exactly that was done here.
Edit: I should’ve added sth like TADAA, disabling javascript and clearing cache finally produces a “device/browser unique fingerprint” not a tab unique one
I can only guess:
Because you use some special apps/programs and/or with a very special setting of preferences, addons etc.
If your fingerprint stays the same after trying something else this page clearly indicates that your own perference of obfuscation was wrong. Compared to all the others out there.
It´s simplyfied down to:
“unique fingerprint by browser at the moment on the machine you´re using atm”
But try thinking out of that box for a moment.
Some times your fingers are dirty … sometimes freshly cleaned.
But they still keep the same basic identification points while in different status.
Imagine: Google, Amazon, and a lot more big data dealers and ad-techs already took dozens of such fingerprints … and they did that over time. Maybe also exchanging them? … Uhh they could win by such a deal, but sshhhh …
They dive deeper and analyze that data depending on their own choices of interesting and less-interesting (=corellating and not correlating) data points. They simply wouldn´t be still in the market if … they would not do that ![]()
I´d like to answer the question on which choices of analysis they are based on. But unfortunately that´s IP and they know to hide it very well.
Back to your example of a CT this means:
There are all these senior-‘Google’-physicans (=analysts) standing around your bed.
Some may say: “same CT analysis … different result. Must be a different ‘patient’.”
But the more experienced ones maybe would add:
“9x % … even more congruent behaviour. Specially on higher rated items. I´d say it´s likely the same person … but maybe that person took a breath. This may explain those unusual data points in those unnormal looking but very selected items.”
PS:
There are no Google-physicans.
Not even Amazon etc. ones.
I think you know it, too ![]()
But they know their data and they use it.
We all may call it AI, data mining etc … a miracle.
Old fashioned ones would rather call it just another boring way of GPU/CPU-driven statistics.
However you call it: it all can be a nice toolset to get much more of information out of a person to influence.
May it be the next product or the next truth (which may be also just a product btw … and sells good atm)
Before I become too pathetic let´s stop it here.
I started with why I see ‘MAC address spoofing’ not as a very appreciated item on my personal topic list and I think I added what needed to be mentioned.
In case you´re looking for a web-page or service that offers privacy advocation.
I know none specific.
In case someone else got a good hint then this would be a good start for a separated thread.
I´d appreaciate suchs links/hints, too.
Best
DonFnord
MAC randomization is confirmed working on Android 11 for FP3 and FP3+ ![]()